I have a fairy typical setup where I have nginx in front of haproxy, where nginx is terminating the ssl connections from client browsers. As our product grew, my loadbalancer machines didn’t have enough CPU to do all the required ssl processing.
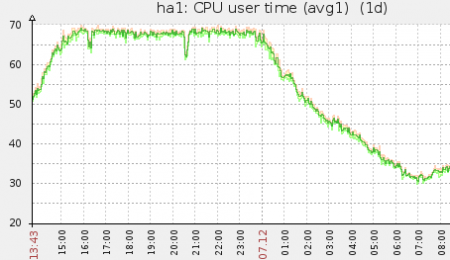
As this zabbix screenshot shows, the nginx takes more and more cpu, until it hits the limit of our AWS c1.xlarge instance. This causes delays for our users and some requests might even time out.
Luckily it turns out that there was a fairy easy way to solve this. nginx defaults, at least in our environment, into a cipher called DHE-RSA-AES256-SHA. This cipher uses Diffie-Hellman Ephemeral key exchange protocol, which uses a lot of CPU. With help from this and this blog posts I ended up with the following sollution:
First check if your server uses the slow DHE-RSA-AES256-SHA cipher:
openssl s_client -host your.host.com -port 443
Look for the following line:
Cipher : DHE-RSA-AES256-SHA
This tells us that we can optimize the CPU usage by selecting faster cipher. Because I’m using AWS instances and these instances don’t support the AESNI (Hardware accelerated processor instructions for calculationg AES) I ened up with following cipher list (read more what this means from here):
RC4-SHA:AES128-SHA:AES:!ADH:!aNULL:!DH:!EDH:!eNULL
If your box can support AESNI you might want to prefer AES over RC4. It’s not the safest cipher choice out there, but more than good enough for our use. Check out this blog post for more information.
So, I added these two lines to my nginx.conf
ssl_ciphers RC4-SHA:AES128-SHA:AES:!ADH:!aNULL:!DH:!EDH:!eNULL; ssl_prefer_server_ciphers on;
After restarting nginx you should verify that the correct cipher is now selected by running the openssl s_client command again. In my case it now says:
Cipher : RC4-SHA
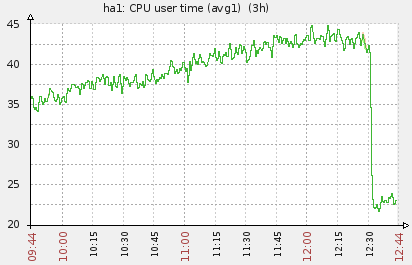
All done! My CPU load graphs also shows a clear performance boost. Nice and easy victory.
One thought on “Optimize nginx ssl termination cpu usage with cipher selection”
Comments are closed.